One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Scott – N8SY and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Scott has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the section will need to use the mailing list link above.
Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
Go to www.arrl.org and logon.
Click Edit your Profile.
You will be taken to the Edit Your Profile page. On the first tab Edit Info, verify your Email address is correct.
Click the Edit Email Subscriptions tab.
Check the News and information from your Division Director and Section Manager box.
Click Save.
Now without further ado…
Read the full edition at:
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
Stay at home: day 42. Continuing to work from home. Haven’t seen co-workers or friends in a month and a half. Regular lunch outings and after work happenings have long since terminated. Virtual meetings and conferences have replaced in person interaction. Participation in Ham Radio activities is on the rise! Nets are seeing higher check-in counts than they’ve ever seen. The curve is rising for digital modes and logged contacts.
Are we all having fun yet during Corona Fest 2020?
As people are forced to work from home due to closures, companies are utilizing videoconferencing services to keep in touch with employees and teams. These are now methods for coordinating efforts and relaying the latest to employees about the status of their company. A videoconferencing solution was likely available for employees to interact with remote team members or vendors world-wide. Now, those services are utilized all-day, every day. My company decided to begin the transition from WebEx to Microsoft Teams for meetings. I liked WebEx and it generally worked. MS Teams, well it’s part of Office 365 and that’s probably down again. Corona Fest is forcing usage of these collaboration solutions, not only companies but social organizations that previously met in person. These include popular names like Skype, Google Hangouts, and Zoom.
 Those who value open sourced solutions should use Jitsi or Jitsi Meet to hold meetings. The service is completely free and open-source where anyone can look at the source code of the project. The difference between Jitsi and Jitsi Meet: Jitsi is a roll-your-own solution meaning you can download server packages or code and deploy an instance however you want. Jitsi Meet Online is an extremely easy-to-use alternative solution for holding meetings – with no installation required.
Those who value open sourced solutions should use Jitsi or Jitsi Meet to hold meetings. The service is completely free and open-source where anyone can look at the source code of the project. The difference between Jitsi and Jitsi Meet: Jitsi is a roll-your-own solution meaning you can download server packages or code and deploy an instance however you want. Jitsi Meet Online is an extremely easy-to-use alternative solution for holding meetings – with no installation required.
 Settings up a meeting is easy as visiting the Jitsi Meet Online link, create a name for the meeting, click Go, set a meeting password, then send out the meeting URL or phone numbers to participants. A meeting can be created in a matter of seconds! Yes, POTS phone service is available as part of the meeting for free. Note, plain old telephone service audio options will not be encrypted due to the nature of the technology. There is nothing to download for desktop PCs with a web browser and most smart devices. Smart phone apps are available for iOS and Android including the F-Droid store. Functionally, Jitsi Meet offers the same features as the others: video, audio, chat, and shared desktop.
Settings up a meeting is easy as visiting the Jitsi Meet Online link, create a name for the meeting, click Go, set a meeting password, then send out the meeting URL or phone numbers to participants. A meeting can be created in a matter of seconds! Yes, POTS phone service is available as part of the meeting for free. Note, plain old telephone service audio options will not be encrypted due to the nature of the technology. There is nothing to download for desktop PCs with a web browser and most smart devices. Smart phone apps are available for iOS and Android including the F-Droid store. Functionally, Jitsi Meet offers the same features as the others: video, audio, chat, and shared desktop.
If I had to pick one thing that I don’t like about Jitsi it is the use of WebRTC. Web Real-Time Communication is also a free and open-source project that provides web browsers and mobile applications with real-time communication (RTC). WebRTC is included in all modern browsers and enabled by default in most. This technology allows audio and video communication to happen without the need
to install additional plugins or apps. Makes it very easy. There are a couple problems with WebRTC in highly privacy focused implementations. One problem is the communication is direct, peer-to-peer. This makes it possible for a skilled individual to learn real Internet Protocol (IP) addresses even while the other is utilizing a VPN. Use of a VPN can allow a user to appear as though their traffic is coming from a different IP and aids in masking actual location. Corporations use VPNs to establish secure communications from their network to their endpoint devices over networks with unknown integrity. Another problem is that end-to-end encryption is not possible with WebRTC. Jitsi addresses this issue in their security document. End-to-end encryption (also abbreviated “E2EE”) is a method where only the communicating users can read messages exchanged, preventing eavesdroppers anywhere along the communication path.
I wish people used better tools such as Jitsi. That’s why there’s choice. I would use this for any meetings I hosted. It seems like a really good open-source alternative to the other solutions.
Zoom became very popular very quickly, almost overnight. It was even recommended right here in last month’s OSJ. Attacks and threats emerge as a result of that popularity and pose risks for users and clubs who are using these services to host meetings. Cyber criminals are crafting email messages to steal logon credentials and packaging malware to look like a Zoom meeting installer.
For most of us, club meetings are not doing anything that’s overly sensitive with Zoom. Some organizations (companies, agencies) banned the use of Zoom citing flaws in the encryption implementation making it easy to exploit and three Chinese companies develop the applications. These should be taken into consideration but there has been no evidence of influence resulting from these issues. Zoom should be commended, though, due to their responsiveness in correcting vulnerabilities and privacy issues that have been discovered in recent weeks.
Free for accounts, everything is managed by the Zoom cloud, including encryption keys. Data is encrypted between the clients and Zoom servers. However, audio is not encrypted if a paid account is using the POTS phone line options.
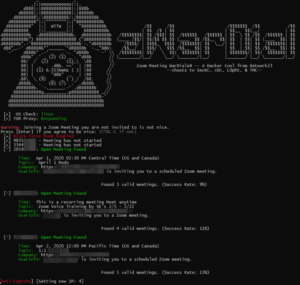
Shortly after its popularity exploded, so did the number of unwanted participants in meetings leading to the term “Zoombombing.” Having someone crash a meeting is obnoxious and an unwanted disruption. Examples of this have made the rounds where Zoom sessions were hijacked by individuals saying or showing things that are lewd, obscene, racist, or antisemitic in nature where everyone in the session can see or hear. Students themselves conspired to have pranksters harass teachers in their online classes. Others utilized ‘Wardialing’ tools to discover unsecured Zoom sessions. Wardialing is an early hacking term where every number in an area code was dialed to find computers, bulletin board systems, servers, and fax machines. The resulting list would be used to guess login credentials and gain unauthorized access to those systems. One person I know had her yoga session crashed by an individual cursing and displaying symbols associated with the National Socialist German Workers’ Party. I have not heard about any disruption to ham radio club meetings.
There are steps the organizer can take or have someone else follow the directions in the Zoom support articles to prevent these issues. Not all of these configuration recommendations are needed for every meeting, follow ones applicable to that meeting. For example, you may not want to lock a club meeting from participants but instead use a waiting room approach.
Latest version: ensure participants are using the most recent client version. In April alone, there have been three updates to the Windows client.
Meeting password: posting a meeting link to social media will draw attention. Send the event password to known users through a direct message or other means where your participants are known.
Waiting room: virtual staging area for guests and participants until you’re ready for them to join.
Manage participants: remove any participants that should not be in the meeting and set who can share their screen.
Disable video, file transfer, annotations, and private chat: cut down on distractions, unsolicited content, or messages as needed.
Accidental removal of a participant: a booted user cannot rejoin a session using the same email address unless a few settings are changed.
Put participants on hold during breaks: attendees audio and video can be disabled during lunch, bio breaks, or private moments.
Video recordings: exercise discretion when recording content and know where that content is stored. Paid customers have the option to record a meeting to the cloud.
Following these tips can lead to a successful, uninterrupted meeting.
I saw a posting by the developer of the MMDVM software, Jonathan – G4KLX. Digital hotspot and repeater owners should follow these guidelines.
This message contains important information that I want disseminated far and wide please. I have been approached by the people who run aprs.fi and REF001/REF030 (not the same people) about problems being caused by hotspots. This is down to usage and I hope that people will act on this information: 1. APRS, it is important that when configuring your hotspot, that you ensure that the suffix used for accessing aprs.fi is unique. For example if you use more than one hotspot, then ensure that for every mode and for every hotspot, the aprs.fi access callsign is unique. This is usually done by specifying a unique suffix to the callsign used by the hotspot. If more than one hotspot attempts to access aprs.fi with the same callsign+suffix combination, the first one is thrown off, and the new one connects. In the meantime the original one tries to connect and throw the new one off. This can happen multiple times per second, and is causing problems for them. Please, please, please, look at your configurations and if you have a duplicate, change one of them. 2. REF001/REF030, apparently the network load on these D-Star reflectors is now very high due to the number of hotspots connecting and staying connected. Could you please consider changing your gateway configuration so that you disconnect after a certain period of inactivity (this means local RF activity) so that they aren't overloaded. I know we like to listen out for activity, but we must also realise that D-Star popular reflectors const money to run, and that includes network and processor usage. A quick look at their dashboards will reveal the problem, they're huge. Jonathan G4KLX
Set unique SSIDs for APRS on different modes and on different hotspots. Finding where APRS information originates isn’t always easy with hotspots. The OpenSPOT 1 has a location information box in settings but it is not transmitted directly by that device, rather Brandmeister pushes that information to the APRS network. Disabling APRS data on the Pi-STAR requires editing the config files and setting priority messages in Brandmeister. The priority message solution should work for OpenSPOT devices too.

Unlink from reflectors, talkgroups, and systems when you’re not using them, especially ones with large numbers of connected users. Users are apparently leaving their devices connected to popular reflectors ting up bandwidth and resources unnecessarily.
To put this into perspective, when I looked at REF001 there were 850 remote/hotspot users connected, about the same on REF030. A mere 12 had transmitted since they were connected. A 5 second transmission is about 9KB worth of Internet traffic. Multiply that by 850 connected devices, that’s 7.6MB of traffic in 5 seconds to connected hotspots, many of which are not being used. That’s an estimated 80 gigabytes or so for an hour-long net. There are ping/heartbeat packets to all connected devices even when the reflector does not have an active radio transmission taking place.
Please check your hotspot APRS configurations and disconnect when not in use.
K8JTK Hub Interlink System
Anyone wanting a place to meet-up for checking on friends and fellow hams or looking for something to do can use a system I’ve been working on the last few months. Currently, it offers 6 full-time ham radio VoIP modes interlinked for interoperability. Ways to access the system:
- EchoLink: K8JTK-R 233196
- AllStar Link: 50394
- Hamshack Hotline: 94026
- DMR: Brandmeister TG 31983
- D-STAR: DCS/XLX983 A
- YSF: K8JTK Hub 17374
Since I’m working from home, I’ve linked up my Wires-X room: K8JTK-ROOM 40680
More information or updates on the system: http://www.k8jtk.org/ham-radio/k8jtk-hub-digital-voip-mutimode-interlink-system/
Thanks for reading and 73… de Jeff – K8JTK
