One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Scott – N8SY and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Scott has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the section will need to use the mailing list link above.
Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
Go to www.arrl.org and logon.
Click Edit your Profile.
You will be taken to the Edit Your Profile page. On the first tab Edit Info, verify your Email address is correct.
Click the Edit Email Subscriptions tab.
Check the News and information from your Division Director and Section Manager box.
Click Save.
Now without further ado…
Read the full edition at: http://n8sy2.blogspot.com/2016/11/november-edition-of-ohio-section-journal.html
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
It’s been a rater busy month. End of the year projects and planning are in full swing. I ran the electronic voting for the LEARA Trustee elections. Voting ended in a never-before-seen tie between two candidates. It was a great slate of candidates and noted in the results because the race was close. There was a clear #1 and #2 winner. The #3 spot was a tie. All three candidates received more than 50% of the total vote. At the Trustees meeting, we sat the two winners then had a run-off vote among the Trustees. Since there were 10 Trustees, the run-off vote could end in a tie so a coin flip may have been the deciding factor. However, the run-off vote did not end in a tie and the 3rd person was seated.
Been planning and getting the end-of-year door prize ready for our Holiday Dinner meeting. Traditionally our club has given away a radio as a door prize at this meeting. For the past two years we’ve given away Baofeng radios. With the findings in the November 2015 issue of QST and similar tests run by other individuals (Dave KD8TWG being one) I encouraged the group to consider better alternatives. We settled on a Yaesu FT-60 HT holiday door prize.
Just this past weekend (10/12), Bill K8SGX with help from KD8TWG (both Technical Specialists) and myself made significant forward progress on installing LEARA’s Fusion Repeater. That project has taken a lot longer than I would like but hit significant road blocks in the original plan. Even installing the repeater at the site caused problems because the handles on the DR1X wouldn’t allow the cabinet to close. *Sigh.* Had to take out the unit, the 16 some screws for the top cover, remove the screws for the handles, and put it all back together. I think one more trip is required to drill some holes and install some jumper cables. Then, finally, it will be on the air *knock on wood.*
If that wasn’t enough, I participated in a DXpedition the weekend of October 22nd. Bob K8MD, Technical Specialist, wrote up an article.
—
 K8JTK, WA8LIV, and myself: K8MD completed a “DXpedition” to South Bass Island to activate Perry’s International Victory and Peace Memorial (NM20) for National Parks on the Air. After an arduous boat ride (wind and waves were high!) we landed on the island around 1045. We started setting up the HF station on Saturday at approximately 1130. We operated for approximately 2 hours on 40m. Operating was great! Once we got spotted, we were frequently piled up. We were averaging over 100 contacts per hour. While the day was relatively sunny, cooler temps and a brisk wind coming off the lake kept us bundled up. The National Park Service was extremely welcoming and hospitable. They offered us tables and chairs, which we declined due to bringing our own. They permitted us to operate on the “back porch” of the museum. So the wind was mostly broke by the building, which was definitely appreciated by us! As long as we kept in the sun, we were comfortable.
K8JTK, WA8LIV, and myself: K8MD completed a “DXpedition” to South Bass Island to activate Perry’s International Victory and Peace Memorial (NM20) for National Parks on the Air. After an arduous boat ride (wind and waves were high!) we landed on the island around 1045. We started setting up the HF station on Saturday at approximately 1130. We operated for approximately 2 hours on 40m. Operating was great! Once we got spotted, we were frequently piled up. We were averaging over 100 contacts per hour. While the day was relatively sunny, cooler temps and a brisk wind coming off the lake kept us bundled up. The National Park Service was extremely welcoming and hospitable. They offered us tables and chairs, which we declined due to bringing our own. They permitted us to operate on the “back porch” of the museum. So the wind was mostly broke by the building, which was definitely appreciated by us! As long as we kept in the sun, we were comfortable.
 The contacts rates never really slowed down much, but it was getting near the time they close the observation deck for the day. So we left the HF setup to head up to the observation deck at 317′ to try a few VHF/UHF contacts on 146.52 (didn’t have SSB capability). We made 7 contacts on FM and zero contacts on DMR. Zero contacts on DMR surprised us, as we had advertised the activation on social media and received responses that people would be out looking for us. We got on the DMR repeaters on the Ohio Talkgroup to try and set up simplex
The contacts rates never really slowed down much, but it was getting near the time they close the observation deck for the day. So we left the HF setup to head up to the observation deck at 317′ to try a few VHF/UHF contacts on 146.52 (didn’t have SSB capability). We made 7 contacts on FM and zero contacts on DMR. Zero contacts on DMR surprised us, as we had advertised the activation on social media and received responses that people would be out looking for us. We got on the DMR repeaters on the Ohio Talkgroup to try and set up simplex  skeds. Even the repeaters were quiet. After coming back down from the observation deck, we operated HF for another 40 minutes until the park closed. At which point we packed up and got dinner. When the day was over, we made approximately 240 contacts on HF and 7 contacts on 146.52.
skeds. Even the repeaters were quiet. After coming back down from the observation deck, we operated HF for another 40 minutes until the park closed. At which point we packed up and got dinner. When the day was over, we made approximately 240 contacts on HF and 7 contacts on 146.52.
We returned to the park on Sunday and operated for an additional 3 hours. From approximately 1200 to 1500. The weather on Sunday was a significant improvement to Saturday afternoon. Sunny skies, calm winds, and temperature around 65. Operating during these three hours however, proved to be more of a duress then the previous day. Both operating and logging proved more difficult due to the lingering effects of the festive activities from the previous evening. When visiting foreign lands, I think it’s important to assimilate into the local culture. We found ourselves in a bar that was both red and round, consuming a strange carbonated gold colored drink, that was dispensed from a tap. Thinking this was just an unusual tasting local water, we consumed a great deal. We wanted to make sure we were properly hydrated and also remain assimilated with the natives. This was Halloween weekend on Put-In-Bay, and everyone was dressed up in costumes. The costumes were quite amazing! Despite the self imposed adverse conditions from our Saturday night activities, we were able to log an additional 100 contacts on Sunday, including DX: Croatia, France, Belgium, Mexico, and Canada. Again the National Park Staff was very warm and welcoming to us. This was the last day the monument and museum would be open this year. The park staff gave us free candy and free popcorn balls at no charge due to the expiration date happening before they reopen in Spring.
 A few different antennas were utilized, as well as a few different methods to get the antennas off the ground. I learned that 40m and 80m dipoles fed with LMR-400 is a lot of weight for my Jackite pole. I need to cut a piece of RG-8X that’s the exact length to get to the base. Then use a connector to connect feed line to get back to the operating position. That should lighten the load on the mast. Despite being stressed, the Jackite pole performed excellent. So much easier to cart around then the military masts I had been using previously!
A few different antennas were utilized, as well as a few different methods to get the antennas off the ground. I learned that 40m and 80m dipoles fed with LMR-400 is a lot of weight for my Jackite pole. I need to cut a piece of RG-8X that’s the exact length to get to the base. Then use a connector to connect feed line to get back to the operating position. That should lighten the load on the mast. Despite being stressed, the Jackite pole performed excellent. So much easier to cart around then the military masts I had been using previously!
 I fabricated an aluminum ground spike for the Jackite pole. Not a good idea: the aluminum ground spike bent under the weight. I guess aluminum was too soft. The point of the ground spike was to hold up the mast while I set the guy wires when operating by myself. We had three people, so it was easy enough for one person to hold up the mast, while the other two set up guy wires. I’m glad I tried the spike for the first time when I had other people around to help me, rather than trying the spike when I was by myself! My portable dipole is a 40m / 80m crossed dipole. The dipole legs are resonant 1/4 wavelength and also act as the guys for the mast. Perhaps I need to try a 40m vertical on the Jackite pole next? A single antenna wire might be more suited to the light weight jackite pole. We used the mast and dipoles on Saturday. Then we used LNR end fedz on Sunday. We used a slingshot / fishing reel to put the end fed into trees. The 40m end fed was up an impressive height. The single band end feds into trees was definitely more simple to set up then setting up the mast and dipoles, and I believe the end fed was just as effective. Both Saturday and Sunday a 20m LNR End Fed was set up vertically in one tree. Since it’s a half wave with match box, it does not require any ground radials. It performed very well with 59 reports into California and Oregon. It’s this antenna where we worked DX stations in Belgium, France, and Croatia.
I fabricated an aluminum ground spike for the Jackite pole. Not a good idea: the aluminum ground spike bent under the weight. I guess aluminum was too soft. The point of the ground spike was to hold up the mast while I set the guy wires when operating by myself. We had three people, so it was easy enough for one person to hold up the mast, while the other two set up guy wires. I’m glad I tried the spike for the first time when I had other people around to help me, rather than trying the spike when I was by myself! My portable dipole is a 40m / 80m crossed dipole. The dipole legs are resonant 1/4 wavelength and also act as the guys for the mast. Perhaps I need to try a 40m vertical on the Jackite pole next? A single antenna wire might be more suited to the light weight jackite pole. We used the mast and dipoles on Saturday. Then we used LNR end fedz on Sunday. We used a slingshot / fishing reel to put the end fed into trees. The 40m end fed was up an impressive height. The single band end feds into trees was definitely more simple to set up then setting up the mast and dipoles, and I believe the end fed was just as effective. Both Saturday and Sunday a 20m LNR End Fed was set up vertically in one tree. Since it’s a half wave with match box, it does not require any ground radials. It performed very well with 59 reports into California and Oregon. It’s this antenna where we worked DX stations in Belgium, France, and Croatia.
A fun time was had by all, and we all look forward to similar opportunities in the future.
Bob Mueller, K8MD
—
This was a phenomenal experience for me as I’ve never done anything close to a DXpedition. Huge thanks to Bob – K8MD as he did much of the planning and most of the equipment used was his. Andrew brought his go box setup for the contacts on Perry’s Monument. We made a total of 350 contacts. Bob worked out the numbers for NM20. We made 3x the average number of contacts for all previous activations. Our contacts accounted for about ¼ of the total number of Q’s through our activation. Thanks to the National Parks Service for their gracious hospitality and putting up with us slinging wires and running coax around the park.
“All your lightbulbs are belong to us”
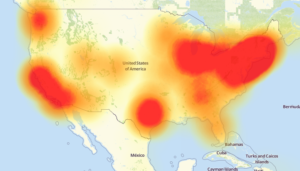
 A pun on the ’90s meme “All your base are belong to us” has been used to describe what happened to the Internet on October 21. There as a massive DDoS attack on one of the companies that provides core services to the Internet. Dyn, formally DynDNS, was the target of this attack. They were known for providing the previously free, now paid, service of allowing automatic updating of DNS records without manual intervention. It was used by tech savvy people to access devices on their home network. I used this service when I ran my website on a server in my house. The Dynamic DNS service would update my URL when the IP address of the DSL modem changed. The company has rebranded to “Dyn” and shifted their focus to more commercial infrastructure products such as domain registration and email services.
A pun on the ’90s meme “All your base are belong to us” has been used to describe what happened to the Internet on October 21. There as a massive DDoS attack on one of the companies that provides core services to the Internet. Dyn, formally DynDNS, was the target of this attack. They were known for providing the previously free, now paid, service of allowing automatic updating of DNS records without manual intervention. It was used by tech savvy people to access devices on their home network. I used this service when I ran my website on a server in my house. The Dynamic DNS service would update my URL when the IP address of the DSL modem changed. The company has rebranded to “Dyn” and shifted their focus to more commercial infrastructure products such as domain registration and email services.
Dyn provides DNS services to some of the largest companies on the internet: Twitter (social media), Reddit (social news aggregation), GitHub (code repository), Amazon (shopping), Netflix (movies), Spotify (music), Runescape (game), and its own website.
DDoS (Distributed Denial of Service) happens when criminals use a large number of hacked, ill-configured, or poorly secured systems to flood a target site with so much junk traffic that it can no longer serve legitimate visitors.
DNS refers to Domain Name System services. DNS is an essential component of the Internet. It’s responsible for translating human-friendly website names like http://arrl-ohio.org/ into numeric, machine-readable Internet addresses (74.220.207.99). Anytime you send an e-mail or browse the web, your machine is sending a DNS look-up request to your Internet service provider (ISP) to help route the traffic.
A DDoS attack effectively makes a site or service disappear from the Internet. Users cannot access the site because it is busy handling (what it believes to be) legitimate traffic but in reality, is junk.
With more and more multi-megabit connections into our homes and more consumer devices on the Internet, the amount of junk traffic generated in recent attacks has been some of the largest seen on the Internet. The availability of tools for compromising and leveraging the collective firepower of Internet of Things devices (IoT) has made these large-scale types of attacks possible. IoT being Internet-based security cameras, digital video recorders, baby monitors, lightbulbs, refrigerators, toasters, and Internet routers – to name a very few. Many of these devices are unpatched, not updated, poorly secured, and essentially unfixable. They’re rushed to market, made as cheaply as possible (which lends little credence to security), and not supported due to lack of resources or the company went out of business. On the flipside, it’s also applicable that users don’t know they need to secure their devices.
Criminals need to build and maintain a large robot network of these devices (known as a ‘botnet’) which is time intensive, risky, and a very technical endeavor. Botnet owners make their services available to anyone willing to pay a couple bucks for a subscription. With a few commands, they can leverage all devices under their control to attack a target. In general, with very few exceptions, owners of compromised devices have no idea their device is part of a botnet.
DDoS attacks are typically: retaliatory in nature – criminals get offended or upset at some comment, story, or statement and, in response, knock their service offline. Attempts at extortion – flood a service with so much traffic it’s unavailable to legitimate users and demand a ransom to stop the attack. Diversion – ‘hey look at this massive attack while we secretly do something else over here.’
It is believed the attack on Dyn was retaliatory in nature using compromised digital video recorders (DVRs) by XiongMai Technologies. The components that XiongMai makes are sold downstream to vendors who then use it in their own products.
A DDoS can happen to anyone or anything connected to the Internet.
I bring up this attack because our Section Manager Scott mentioned it in one of his mailings and I was discussing it with Bob – K8MD on our DXpedition. Bob indicated he was seeing a lot of posts online how something similar could disrupt ham radio digital modes and hams must stick to analog only modes. His response was: a digital repeater will still function without the Internet, which is true. D-STAR, DMR, Fusion, and probably any other up-and-coming mode repeaters will still continue to operate without an Internet link. Additionally, all of these modes will operate simplex without a repeater and without infrastructure. The Internet is for linking or sending your message to another endpoint. Then you have resources like PSK31 or Olivia that do not have any Internet infrastructure component. Digital modes, in particular on the HF bands, can reach out further than analog modes.
I think it would be possible to make a backup IP link over another transport (like Mesh) for those modes or use AllStar – which is great for linking over non-Internet based networks. To go even further with the dooms-day scenario: if anyone else can get access to your resources, they have the potential to disturb them. Analog repeaters too can be jammed, brought offline with a power outage, or sabotaged by a determined actor.
How can we fix DDoS attacks? We can’t. The Internet and the protocols in use today are not much different than originally designed. The protocols were not designed to handle this type of abuse. Strides are being made by ISPs so secure their networks as best they can. There is even dissent between providers as to what steps should be taken. Another suggestion is to create some kind of IP security association with published standards, auditing, and a certification process similar to an Underwriters Labatory “UL” sticker on a product. Another (less likely) is to hold companies financially responsible for attacks using their devices. Less likely to happen because it could put legitimate companies out of business quickly and would not hold fly-by-night companies responsible. Until then, these devices will remain a danger to others until they are completely unplugged from the Internet. That’s not going to happen. We like our stuff.
Coverage of the DDoS and resources used for my write-up:
https://krebsonsecurity.com/2016/10/ddos-on-dyn-impacts-twitter-spotify-reddit/
https://krebsonsecurity.com/2016/10/hacked-cameras-dvrs-powered-todays-massive-internet-outage/
https://twit.tv/shows/security-now/episodes/583
img: http://www.joyoftech.com/joyoftech/joyarchives/2340.html
Map is of the outages caused by the attack.
That’s about it for this month. Thanks for reading and 73… de Jeff – K8JTK