One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Scott – N8SY and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Scott has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the section will need to use the mailing list link above.
Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
Go to www.arrl.org and logon.
Click Edit your Profile.
You will be taken to the Edit Your Profile page. On the first tab Edit Info, verify your Email address is correct.
Click the Edit Email Subscriptions tab.
Check the News and information from your Division Director and Section Manager box.
Click Save.
Now without further ado…
Read the full edition at: http://n8sy2.blogspot.com/2016/03/march-edition-of-ohio-section-journal.html
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
It’s been a busy month for yours truly. Things got started off with a drive down to Columbus with my dad N8ETP. We visited the Columbus Radio Enthusiasts Society (CRES) on February 16th. It was touch-and-go for a while due to the weather. Snow hit both areas the night before and hoped it would hold off for the meeting. It did. We made it there and back, no problem. It was our first meeting in Columbus and we couldn’t have had a better time. I was contacted by Steve – N8WL to troubleshoot an RFI issue he was experiencing.  We got to talking and he invited me to come down and speak about, well, myself –what the Technical Coordinator does and projects I’ve worked on. The presentation consisted of: my history in Ham Radio and how I got to where I am, laid out the ARRL and Field Services structures, section level positions and the Ohio Section, my responsibilities as Technical Coordinator, and projects I’ve worked on. In addition gave some pointers for troubleshooting RFI problems. Our Section Manager was on hand and helped answer specific questions about the section. It was an informative meeting. CRES: http://www.w8zpf.net/, presentation: http://www.k8jtk.org/2016/02/16/about-the-arrl-ohio-section-technical-coordinator/
We got to talking and he invited me to come down and speak about, well, myself –what the Technical Coordinator does and projects I’ve worked on. The presentation consisted of: my history in Ham Radio and how I got to where I am, laid out the ARRL and Field Services structures, section level positions and the Ohio Section, my responsibilities as Technical Coordinator, and projects I’ve worked on. In addition gave some pointers for troubleshooting RFI problems. Our Section Manager was on hand and helped answer specific questions about the section. It was an informative meeting. CRES: http://www.w8zpf.net/, presentation: http://www.k8jtk.org/2016/02/16/about-the-arrl-ohio-section-technical-coordinator/
The following weekend I presented at the Mansfield Hamfest during the Digital Forum. Danny – W8DLB, who is in charge of the Hamfest, was at my NBEMS training session in Medina County and asked me to present it during the Digital Forum. The Digital Forum covered voice and text based digital modes. Duane -K8MDA demonstrated FreeDV. FreeDV is a mode used on HF for voice communication. It’s impressive because the bandwidth is about one-third of sideband! I gave a portion of my training session on Narrow Band Emergency Messaging using Fldigi.
 At the LEARA meeting in Cleveland, I showed the video for the Navassa Island K1N DXpedition which happened in February of last year. A DXpedition is an expedition to a remote location, usually uninhabited, for the purposes of activating the location and making as many contacts as possible. Navassa was my first time trying to chase a “most wanted” entity for my log. I was able to log them twice. Bob Allphin – K4UEE has participated in many DXpeditions and has released the story of many on DVD. I had no idea what it took to put on a DXpedition of that magnitude. After seeing his DVD on Navassa, I now have a better idea. It is a phenomenal video that got rave reviews and comments at the meeting. The main video runs about 45 minutes. The wrap-up from the Dayton forum is included which has some great background details. These are great for club meetings, introducing newcomers to Ham Radio, and gifts. Purchasing the video helps supports future DXpeditions and supports other hams: http://t-rexsoftware.com/k4uee/dvds.htm
At the LEARA meeting in Cleveland, I showed the video for the Navassa Island K1N DXpedition which happened in February of last year. A DXpedition is an expedition to a remote location, usually uninhabited, for the purposes of activating the location and making as many contacts as possible. Navassa was my first time trying to chase a “most wanted” entity for my log. I was able to log them twice. Bob Allphin – K4UEE has participated in many DXpeditions and has released the story of many on DVD. I had no idea what it took to put on a DXpedition of that magnitude. After seeing his DVD on Navassa, I now have a better idea. It is a phenomenal video that got rave reviews and comments at the meeting. The main video runs about 45 minutes. The wrap-up from the Dayton forum is included which has some great background details. These are great for club meetings, introducing newcomers to Ham Radio, and gifts. Purchasing the video helps supports future DXpeditions and supports other hams: http://t-rexsoftware.com/k4uee/dvds.htm
Last, and certainly not least, Ken – KG8DN instructor at Gilmour Academy in Gates Mills, Ohio has been in charge of the Gilmour Academy Radio Club – ND8GA for as long as I’ve known him. During the school year, organizations are in charge of running Convocation for a week. This is a gathering of the entire school for announcements, happenings, events, and entertainment. Ken asked me to speak at Convocation one morning. This was a different type of presentation than I was expecting. I figured I would be there to talk-up Ham Radio and get kids interested. Nope. It was more about life experiences with a little Ham Radio sprinkled in. Things students could relate to. I have to be honest this was more challenging than I anticipated. A lot of time was spent searching for topics that students would care about, relate to, and how those experiences got me to where I am now. There was a visual portion which included many pictures from my high school years. When looking back on friends and people I shared those experiences with, it make me wish I was back in that time. I’m sure I’ll feel the same way when I look back on today. The presentation turned out great and I have to thank Ken for all of his help. ND8GA: https://sites.google.com/a/gilmour.org/gilmour-amateur-radio-club/
Thank you to everyone for coming to my various appearances and the organizers for asking me to speak with your organizations.
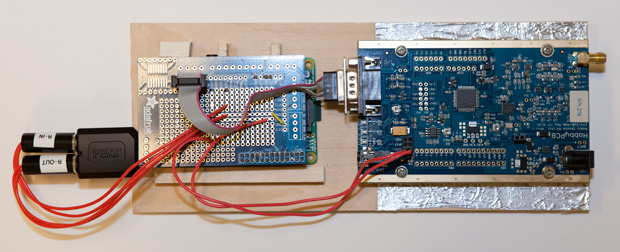
 I received an email from a fellow Trustee of LEARA, Marv – W8AZO, asking if I had seen my name mentioned in a post on a website. I had not. What website did he find my name on? The IEEE website. Now, I know the fine folks over at IEEE (Institute of Electrical and Electronics Engineers) are wicked smart. Much smarter than I am. They come up with solutions to technical problems which usually turn into established standards. Additionally, they publish one-third of the world’s technical literature. Why the heck would they be talking about me? Stephen Cass – KB1WNR, Senior Editor for the IEEE Spectrum magazine wrote an article titled “Hands on: A Ham Radio for Makers.” He built an FM transceiver using an RS-UV3 transceiver board and Raspberry Pi to take advantage of digital modes. I was mentioned because Stephen used the instructions I posted to compile and run Fldigi on the Raspberry Pi. Super cool!
I received an email from a fellow Trustee of LEARA, Marv – W8AZO, asking if I had seen my name mentioned in a post on a website. I had not. What website did he find my name on? The IEEE website. Now, I know the fine folks over at IEEE (Institute of Electrical and Electronics Engineers) are wicked smart. Much smarter than I am. They come up with solutions to technical problems which usually turn into established standards. Additionally, they publish one-third of the world’s technical literature. Why the heck would they be talking about me? Stephen Cass – KB1WNR, Senior Editor for the IEEE Spectrum magazine wrote an article titled “Hands on: A Ham Radio for Makers.” He built an FM transceiver using an RS-UV3 transceiver board and Raspberry Pi to take advantage of digital modes. I was mentioned because Stephen used the instructions I posted to compile and run Fldigi on the Raspberry Pi. Super cool! 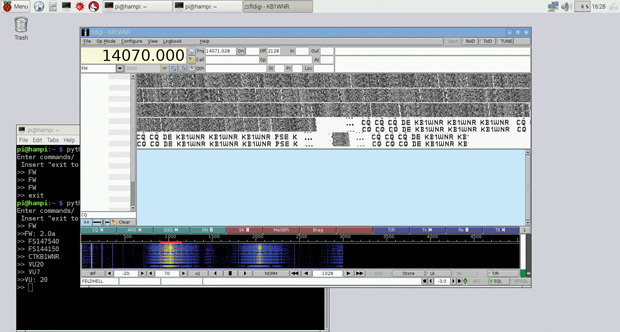 I emailed Stephen and thanked him for the plug. He was very appreciative of the well written instructions. His article may have glossed over some important points relevant to hams but the goal of the article was to draw others in from the wider community. The article will be in the March printed edition of IEEE Spectrum and should be available by the time you read this. It hasn’t hit the shelves in my local bookstore yet. Online version: http://spectrum.ieee.org/geek-life/hands-on/hands-on-a-ham-radio-for-makers
I emailed Stephen and thanked him for the plug. He was very appreciative of the well written instructions. His article may have glossed over some important points relevant to hams but the goal of the article was to draw others in from the wider community. The article will be in the March printed edition of IEEE Spectrum and should be available by the time you read this. It hasn’t hit the shelves in my local bookstore yet. Online version: http://spectrum.ieee.org/geek-life/hands-on/hands-on-a-ham-radio-for-makers
That is what ham radio and makers are all about. I wanted to figure out how to run Fldigi on the Raspberry Pi, came up with a way to do it, documented it thoroughly, and shared it online. Stephen came across my instructions and used them as part of his project to create something greater; perpetuating the cycle.
Thanks for reading and 73… de Jeff

